Supply Chain Attacks: How They Work and How to Protect Your Business in 2025
.png)
Introduction
Supply chain attacks have emerged as one of the most pressing cybersecurity threats in 2025. Instead of targeting a company head-on, attackers infiltrate trusted vendors, third-party software, or external scripts to compromise the final target. This indirect method makes them harder to detect and often far more damaging.
With global organizations increasingly reliant on cloud services, SaaS platforms, and third-party marketing scripts, attackers are exploiting weak links in the digital ecosystem. The results can be catastrophic: massive data breaches, financial losses, regulatory penalties, and irreparable brand damage.
According to the U.S. Cybersecurity & Infrastructure Security Agency (CISA), supply chain attacks are particularly dangerous because they “undermine trust in software and services that organizations rely on every day.” From the SolarWinds breach that exposed U.S. federal agencies to Magecart campaigns siphoning customer credit card data, these incidents are no longer isolated — they are mainstream.
In this article, we’ll break down:
- What supply chain attacks are and how they work.
- High-profile examples from recent years.
- Why these attacks are uniquely dangerous.
- Practical steps for prevention, including solutions like Spider AF SiteScan that defend against script-based attacks.
What Is a Supply Chain Attack?

A supply chain attack occurs when cybercriminals compromise a third-party vendor, service, or script that an organization relies on. Instead of breaking into a company directly, attackers infiltrate through the trusted “suppliers” of software, hardware, or digital services (Cloudflare).
Common forms include:
- Software supply chain attacks
- Malicious code is inserted into legitimate software updates.
- Example: the SolarWinds Orion compromise.
- Third-party script attacks
- Marketing and analytics scripts loaded on websites are hijacked.
- Example: Magecart attackers injecting malicious JavaScript into payment forms (Fortinet).
- Hardware & component attacks
- Malicious chips or tampered hardware enter IT environments.
- Cloud and managed services compromises
- Attackers breach managed IT providers, gaining access to all client environments.
Because organizations rarely control every dependency, attackers exploit this “trust gap.”
Real-World Examples of Supply Chain Attacks
- SolarWinds Orion (2020):
Hackers compromised SolarWinds’ Orion software updates, exposing 18,000 organizations including Fortune 500 companies and U.S. government agencies (CrowdStrike). - British Airways (2018):
Malicious JavaScript injected on BA’s payment page leaked 380,000 payment records, resulting in a £20 million fine under GDPR (UK NCSC). - Ticketmaster (2018):
Attackers compromised a third-party chatbot provider, exposing 40,000+ customer records (BlueVoyant, 7 Examples). - Kishiwada Sports EC site (2024, Japan):
A Japanese sports retailer suffered a 13,879 credit card breach via malicious scripts on its e-commerce site (Spider AF SiteScan deck). - Codecov (2021):
Attackers tampered with a software update, giving them access to thousands of developers’ credentials and source code (Wikipedia). - Dependency Confusion Attacks (2021):
Security researcher Alex Birsan showed how uploading malicious packages to public repositories (npm, PyPI) could trick companies into downloading malware (CrowdStrike).
These examples show that supply chain attacks target trust itself — in vendors, in updates, and in widely used digital tools.
Why Supply Chain Attacks Are So Dangerous

Unlike typical breaches, supply chain attacks scale exponentially. One compromised provider can cascade to thousands of clients. Some reasons they’re uniquely dangerous:
- Widespread impact: A single vulnerability in one vendor can affect thousands of organizations simultaneously.
- Stealthy nature: Malicious code often hides in trusted updates or legitimate-looking scripts, bypassing traditional defenses.
- Regulatory pressure: New standards like PCI DSS 4.0.1 (effective March 31, 2025) require businesses handling credit card data to secure client-side scripts (Spider AF SiteScan). Non-compliance risks fines, lawsuits, and reputational damage.
- Brand trust erosion: Customers are far less forgiving of companies that fail to protect their personal data.
Research also shows that 60% of small businesses close within six months of a major cyberattack due to lost trust and financial burden (BlueVoyant).
How to Prevent Supply Chain Attacks
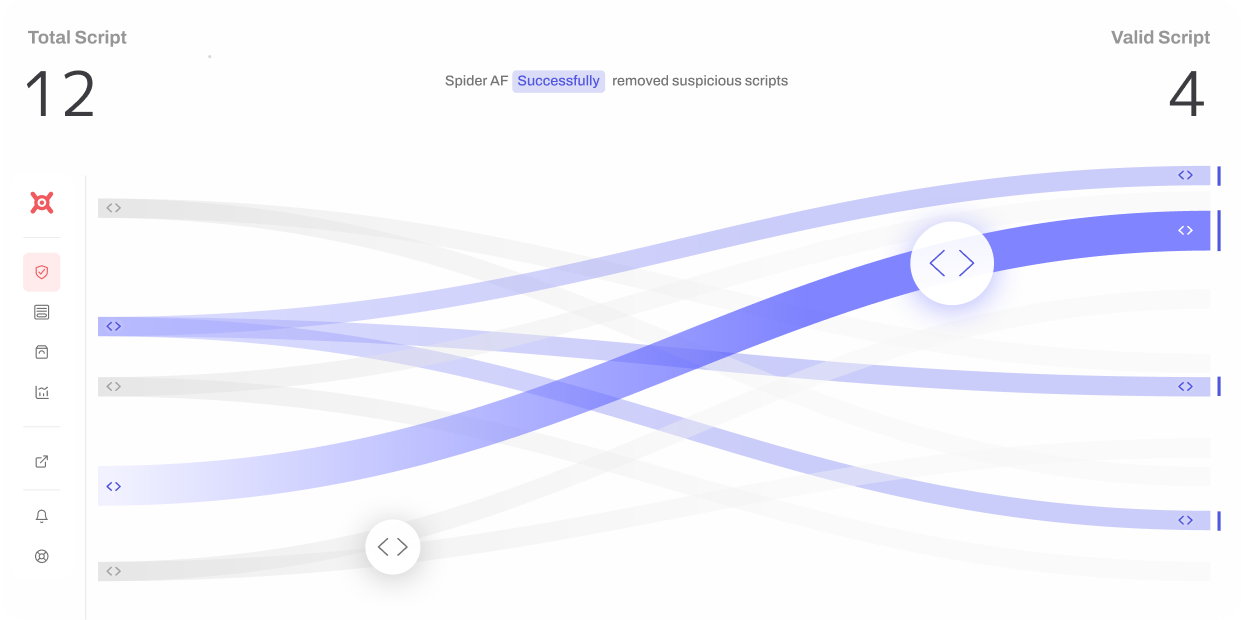
Defending against supply chain attacks requires layered security and vendor oversight. Best practices include:
- Vendor Risk Management
- Regularly audit suppliers for security practices.
- Require compliance with ISO 27001, SOC 2, or PCI DSS.
- Software Bill of Materials (SBOMs)
- Maintain transparency into all software components and dependencies.
- Continuous Monitoring of Third-Party Scripts
- Real-time detection of tampered scripts and unauthorized data exfiltration.
- Zero-Trust Security Model
- Don’t assume trust even within “approved” tools or services.
- Client-Side Security with Spider AF SiteScan
- Modern attacks like Magecart exploit scripts running in the browser, outside server protections.
- Spider AF SiteScan provides real-time monitoring of scripts, anomaly detection, and AI-driven risk scoring.
- It visualizes all third-party tags, tracks data transmissions, and blocks unauthorized behavior — helping companies stay compliant with PCI DSS 4.0.1 and avoid BA/Ticketmaster-style breaches.
👉 SiteScan essentially acts as a “security camera for your website scripts.”
FAQ: Supply Chain Attacks
Q1: Who is most at risk of supply chain attacks?
Any business that relies on third-party vendors, especially e-commerce, SaaS platforms, and financial services.
Q2: Are supply chain attacks the same as phishing?
No. Phishing targets individuals with fraudulent messages. Supply chain attacks target organizations indirectly by infiltrating their trusted partners or tools.
Q3: How can e-commerce businesses specifically prevent supply chain attacks?
By monitoring third-party scripts (analytics, payment tags, chatbots) for unauthorized changes. Tools like Spider AF SiteScan are designed for this exact use case.
Q4: What regulations apply to supply chain security in 2025?
- PCI DSS 4.0.1 (client-side script monitoring for credit card data).
- GDPR (Europe).
- CCPA/CPRA (California).
- Increasingly, vendor security audits are becoming a contractual requirement.
Conclusion
Supply chain attacks exploit the trust businesses place in their vendors, scripts, and software. From SolarWinds to Magecart, the last decade has shown how devastating these attacks can be. With the growing complexity of digital ecosystems, the risks in 2025 are greater than ever.
The good news? Proactive measures like vendor audits, SBOMs, and continuous client-side monitoring significantly reduce exposure.
That’s where Spider AF SiteScan comes in. By providing real-time monitoring, anomaly detection, and compliance support, it helps businesses stay ahead of attackers — before small script changes turn into multimillion-dollar breaches.
👉 Protect your website today with a free SiteScan diagnosis and secure your supply chain against tomorrow’s threats.



















